Mobile technologies are constantly being developed and released into the marketplace with wireless being touted as the solution to accessing networks and the web whilst on the go. This is going to come into play more and more in education and if schools want to implement wireless solutions, then we'd better have some people on staff who can make informed decisions about what it all means. With that in mind, Robyn, our network manager enrolled herself and got me as well to go to a Wireless Network Seminar held in the city at the very swish Radisson Playford hotel. It wasn't strictly aimed at education but was being provided free by intechnology.com.au and was officially titled "The Basics and Fundamentals of 802.1x Wired, Wireless and EndPoint Security”. Not what I'd normally sign up for but anything that adds to my general knowledge about computer technology is a good thing. Plus we do have longer term plans to introduce wireless hotspots at our school with maybe a set of laptops so I was hoping to soak up some information.
There were a lot of blokes in suits with flashy PDA's that made my battered old Ipaq look a bit dated, and a severe gender inbalance where each female attendee was outnumbered 10 to 1. There were a few education faces there as well - I overheard a few people introducing themselves to each other as being from some of the more expensive, up market private schools. I was surprised by the age of the crowd as well - a lot of older faces while I thought IT was a young person's industry.
That was shown by the first speaker who looked like he was still in the beginning stages of his twenties. His name was Neal Wise, who is what is known as an ethical hacker. He specialises in setting up secure wireless networks and check for security loopholes in existing setups. His company is assurance.com.au and he had an education connection as his company built a secure wireless network for the Victorian Dept. Of Ed. with 10, 000 access points across 1800 sites. So he started by showing us an image of a building covered in dishes and aerials - leased out to various wireless companies. He said that wireless is often implemented before the security surrounding the network is mature enough to do its job. He had a great quote that went along the lines of "Technology tries to jump around and avoid the problems created by itself." Different products are continually being developed for different frequencies to avoid traffic overload and interference. Every time you open your wireless note book it automatically searches for networks, known and then unknown. This then could be compromised by someone else's wireless that deliberately seeks to use your notebook connection to access your network. An open wireless network means someone else could steal your bandwidth. He talked about common technologies used to secure wireless which was very informative, having only encountered these acronyms when I was setting up my home wireless router. He talked first about WEP - this only provides basic security, can be breached on a network basis - certain things can still be accessed - ie. SSID. The next technology to evolve from WEP is WPA which has greater security.
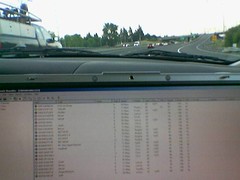 The part that was most fascinating for me was when Neal talked about the practice of wardriving. This is also close concept wise to warchalking which involves finding an open network and chalking the details on the sidewalk so others can access the insecure wi-fi. Neal seemed to think that this was a bit of an urban myth. For his wardriving (remember he is an ethical hacker which means he tries to breach wireless security for a living!) Neal used a GPS system, antenna, software for interrogation and a system to run the software. He told us about one job where his team "staked out" a warehouse that was unaware of their surveillance but under contract from the warehouse head office. The antenna used was actually bits and pieces taped together! He showed an image of his Commodore wagon showing his "get out of jail" card, the official letter that explained his activities to anyone from security (the big burly type) who wanted to know what they were up to. He did explain that this was necessary as computer experts weren't renown for their strength! He showed us a few of the hacking tools he used and showed us live what wireless activity he could detect from the hotel window and showed us how he detects and then "attacks" an insecure network to fully expose its weaknesses. That was amazing but hacking in this way is not a quick process. To crack a WEP encryption takes 1.2 - 1.8 G of data before it can be unlocked, and 15 minutes to 1 hour to get the key but while this going on, it is obvious from within the network that it is being breached. As he pointed out, any use of these tools cross the line of "if you're not authorised to use a network, then you shouldn't be accessing it." The important detail Neal emphasised was any encryption is better than none because it prevents accidental connection. He was a great speaker and I really enjoyed a peek into this world that clearly tells me that my ICT savvy is very shallow compared to these very talented people who design and troubleshoot security for all of our digital data that we take for granted.
The part that was most fascinating for me was when Neal talked about the practice of wardriving. This is also close concept wise to warchalking which involves finding an open network and chalking the details on the sidewalk so others can access the insecure wi-fi. Neal seemed to think that this was a bit of an urban myth. For his wardriving (remember he is an ethical hacker which means he tries to breach wireless security for a living!) Neal used a GPS system, antenna, software for interrogation and a system to run the software. He told us about one job where his team "staked out" a warehouse that was unaware of their surveillance but under contract from the warehouse head office. The antenna used was actually bits and pieces taped together! He showed an image of his Commodore wagon showing his "get out of jail" card, the official letter that explained his activities to anyone from security (the big burly type) who wanted to know what they were up to. He did explain that this was necessary as computer experts weren't renown for their strength! He showed us a few of the hacking tools he used and showed us live what wireless activity he could detect from the hotel window and showed us how he detects and then "attacks" an insecure network to fully expose its weaknesses. That was amazing but hacking in this way is not a quick process. To crack a WEP encryption takes 1.2 - 1.8 G of data before it can be unlocked, and 15 minutes to 1 hour to get the key but while this going on, it is obvious from within the network that it is being breached. As he pointed out, any use of these tools cross the line of "if you're not authorised to use a network, then you shouldn't be accessing it." The important detail Neal emphasised was any encryption is better than none because it prevents accidental connection. He was a great speaker and I really enjoyed a peek into this world that clearly tells me that my ICT savvy is very shallow compared to these very talented people who design and troubleshoot security for all of our digital data that we take for granted.
Photo Credit: 1092835800 by wonko, Flickr Creative Commons Images.

 The part that was most fascinating for me was when Neal talked about the practice of
The part that was most fascinating for me was when Neal talked about the practice of